
“7 for all mankind” (7FAM) is a California based brand that sells premium denim wear world-wide. Besides less severe issues with their online shop, they expose sensitive information about their clients like addresses, phone numbers and order details publicly. The flaw was found by chance while using their online shop as a customer.
I will not take credit for any fancy research, anyone could have found this - starting with 7FAM testers, operators and auditors. The overall experience with this case makes it very clear to me that there are no business processes in place to avoid and handle incidents like this. The company appears to primarily consist of marketing, sales and customer service. I run a bug bounty program myself and don’t expect response times like an IT company that deals with vulnerabilities on a daily basis. However, the actual response besides “oh, thats unfortunate” was effectively zero. I don’t blame people for doing their jobs but i am very disappointed by the organization failing to create any awareness.
Disclaimer
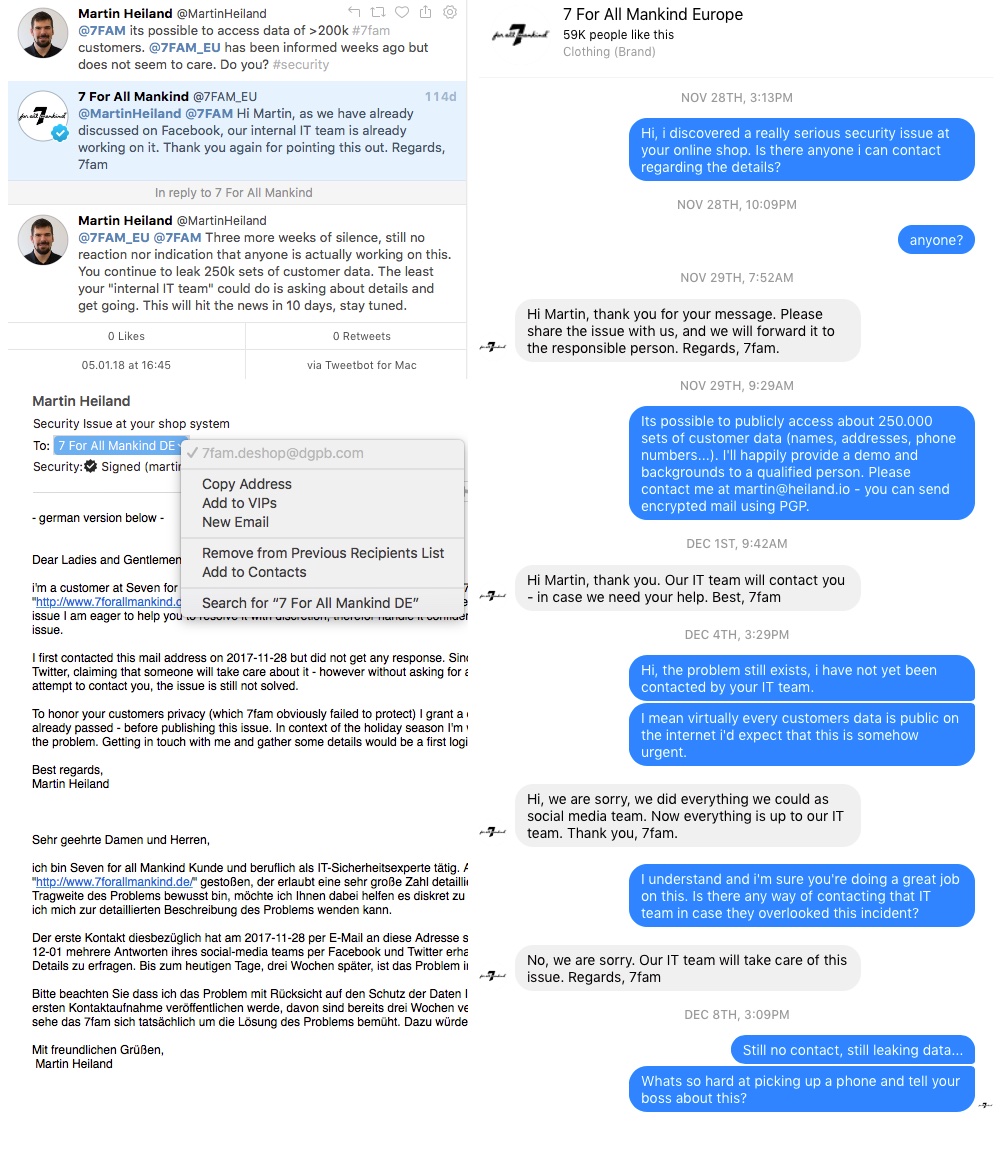
7FAM was informed back in November of 2017 and I offered to pinpoint and eventually stop the leak. Although communicating on multiple channels i never got any response indicating that someone takes action or at least cares about the topic. Apparently protecting customer data and IT systems in general has no priority for 7FAM and their security strategy is to kick the can down the road. Since the issue was reported half a year ago and is trivial to find, i decided to publish information although the issue is not fixed to date.
My hope is to get the attention of someone within the organization to take this serious since bad guys have or will potentially discover this flaw anyway. At the same time i feel sorry for those individuals which data got exposed by a weak security concept and even worse “management” by 7FAM. At several occasions i mentioned that i will publish this issue six WEEKS after calling it in. Now, after six MONTHS i run out of patience.
Disclosure timeline
- 2017-11-25 Discovery of the flaw, created demo script
- 2017-11-25 Attempt to established contact (Mail) no response
- 2017-11-27 Attempt to established contact (Twitter) no response
- 2017-11-28 Attempt to established contact (Contact Form) no response
- 2017-11-28 Attempt to established contact (Website Chat) no response
- 2017-11-28 Attempt to established contact (LinkedIN) no response
- 2017-11-28 Attempt to established contact (Facebook Messenger) no response
- 2017-12-01 First response by 7FAM via Facebook Messenger, rather useless
- 2017-12-11 More useless responses via Twitter
- 2017-12-16 Telephone call with customer service
- 2017-12-17 Several E-Mails to a address given to me, no response
- 2018-01 Many more E-Mails with customer service, got responses but no action was taken
Overview
When you order something at 7FAM online shop, you create an account, set a password and get access to your customer area. Then when purchasing, you get a mail confirmation and later on a receipt with a link to an invoice. Your order appears to be safely accessible through your customer area, however this is not the whole story.
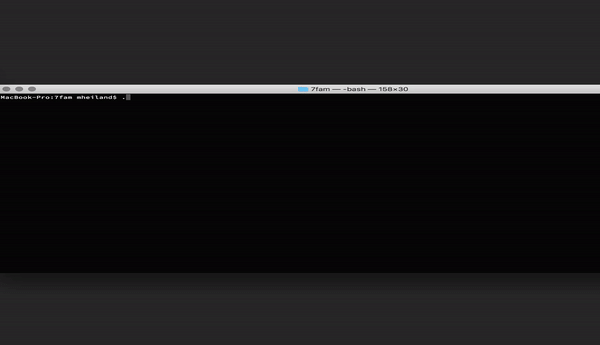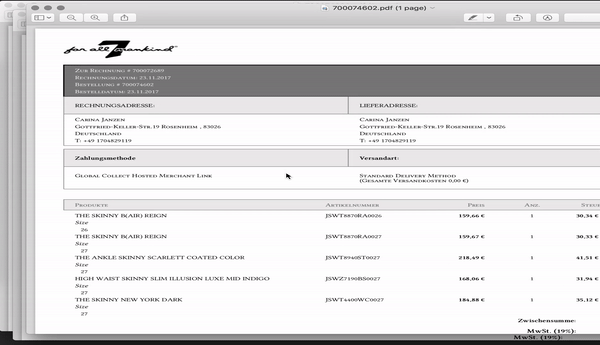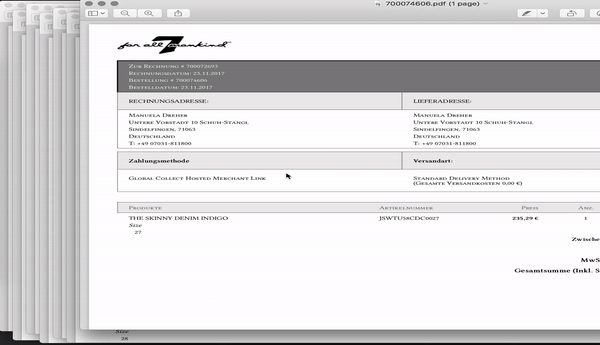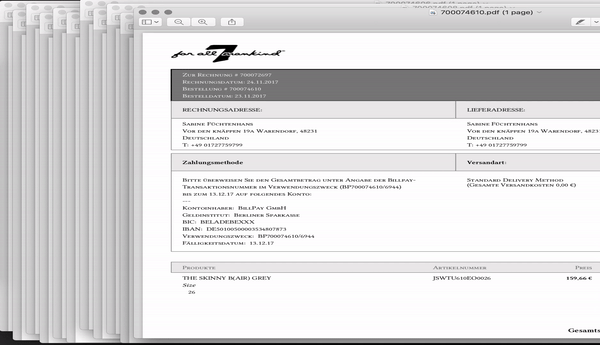
For whatever reason, 7FAM undermines their “customer area” and offers a PDF version of each invoice without authentication. I noticed this when clicking the “download PDF invoice” link at their mails and wondered: “Wait a minute, i logged out - why can i still access my invoice?”
Taking a deeper look made it clear that the “Download invoice” link does not contain any one-time token and not even a pseudo-random path which would make it harder to guess. In fact, every invoice gets an identifier and - yes you have guessed correct - this is an incrementing number.
Now the fun part starts, its not just my invoice which i can access, but rather every invoice of each online purchase made at their european online store since 2011. Ugh! Needless to say that there is no rate limit, expiration or other countermeasure to slow down access to invoices.
So i wrote a script and tried some combinations of identifiers. I ended up with a list of all valid countries and range of invoices. In total, 7FAM publishes about 250.000 invoices.
Playing with numbers
A typical 7FAM order ID looks like 700012345 - sorry Ruth, please complain at 7FAM.
The first part 70 is static and identifies the country at which the purchase was made, for example:
- 70 (Germany)
- 60 (UK)
- 11 (France)
The second part 0012345 is the unique and incrementing order identifier.
When downloading the invoice, a URL like this is called:
https://www.7forallmankind.de/de_de/sales/pdf/pdfinvoices?order_id=000000000
As a fun fact HTTPS is used to secure data in transit, which is completely useless since there is no authentication. At least we can be sure that the invoice originates from the advertised source :-D
There are plenty of unprotected invoices out there, judging from the last valid invoice ID.
| Country | Amount |
|---|---|
| Germany | 75.000 |
| United Kingdom | 63.000 |
| Netherlands | 32.000 |
| Belgium | 21.000 |
| France | 14.000 |
| Italy | 6.000 |
| Ireland | 1.500 |
| Spain | 1.000 |
| Total | 231.500+ |
Impact
Now, asking the obvious: what could someone do with this? Such invoices contain personal information like address, phone numbers, payment and shipping data, gender, body metrics and financial capabilities. Taking the typical demography of 7FAM customers into account, this makes the leaked data very valuable for unsolicited advertising, data validation, data enrichment, identity theft, harassment and stalking. This flaw also provides insights to internal 7FAM sales metrics for the region.
One aspect is really ugly, which is stalking. There are a lot of sick fucks out there that would really like to get a list of wealthy women around them that wear size 27 skinny jeans. 7FAM just provides them this data and they even get a phone number on top. I’m quite sure 7FAM customers would agree that this is a major breach.
Despite being mentioned multiple times during conversations with 7FAM, their “Internal IT Team” did not ever contact me. Interestingly enough my requests to help and provide details were shut down with “IT is working on it” nonetheless. It’s beyond my imagination what they were working on while apparently not knowing anything about the leak.
This whole process is a sad prime example for how NOT to handle security incidents. Such things will not just go away and rejecting help without having any information at hand is rather pointless. Denial will not get you anywhere, its all about having the right means, knowledge and awareness within your organization. Not just because GDPR tells you to…