Holiday time, home network improvement time :)
IPv6
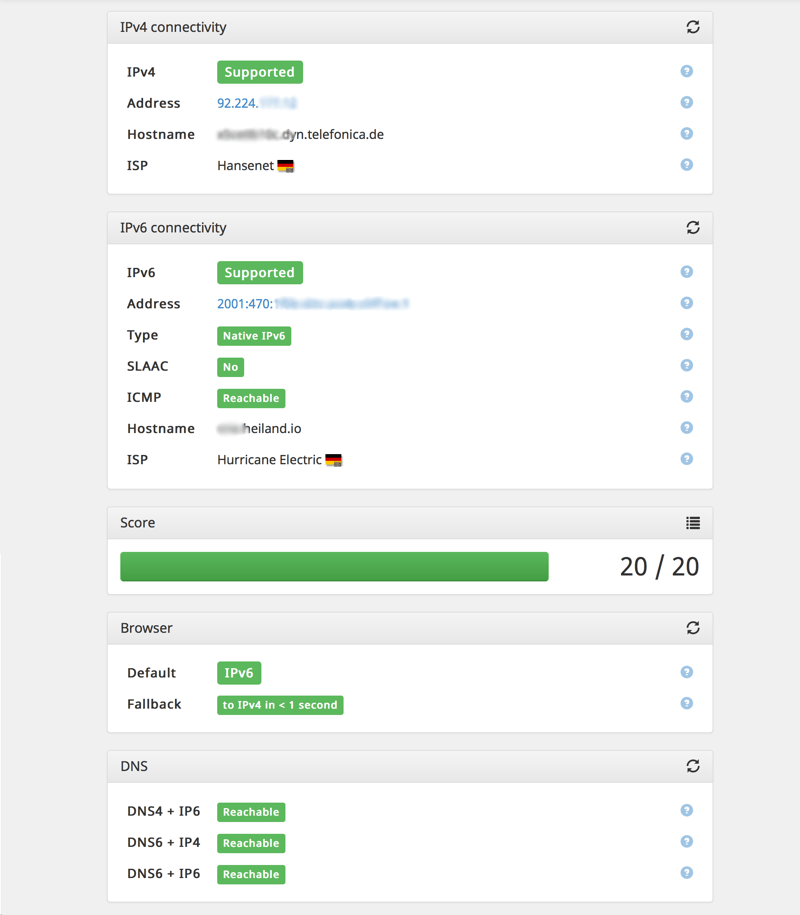
like most ISPs in Germany, Telefonica/O2 STILL does not provide IPv6 to their residential customers. During the past year i’ve been using the IPv6 tunnel broker offering from Hurricane Electric (HE). A alternative service would have been SixXS, but besides having multiple local PoP, it lacks some functionality and i had very bad experience with their support team. Being called a liar and getting insulted because of a typo or overcautious fraud detection system is not nice guys.
HE provides you with a /64 network and a optional /48 if 18446744073709551616 hosts simply don’t cut it and you rather need 1208925819614629174706176. HE turned out to be super reliable, fast and of great value - well, it’s free. The documentation is a bit scarse and the user interface obviously targets experienced users. However, i made my way through and also migrated my domains DNS/rDNS services there. A real killer-feature is the included DDNS (Dynamic-IP-to-DNS mapping) option, so you can update and assign a dynamic IP to a regular A or AAAA record without CNAM’ing via one of those dyndns domains. Especially mail servers don’t like CNAMEs for sender domain/servers. Thanks HE, you’re awesome!
Now, having my router configured for DDNS and tunneling IPv6 is one thing but i wanted to use native IPv6 for all clients within my home network. Turns out that dd-wrt, which powers my Asus RT-AC66U router, has solid support for RA (Router advertisement) and DHCPv6. Certain features do not work reliable with specific dd-wrt beta (aka. recent) builds so i had to trial&error myself to “v3.0-r27858 giga” to find a “good” build. Configuring IPv6 is straight forward but some components, especially wide-dhcp6, are very picky about their syntax and not very verbose when it comes to errors. Therefor i’m sharing the configuration, i hope it will help others and spare some frustration.
A central thing to understand with IPv6 is that DHCP works a bit different compared to IPv4. In good’ol IPv4 DHCP provided clients with information about DNS, Gateway/Router, Subnets and of course a IP address. With IPv6 those tasks are split between RA and DHCP. RA takes care about providing router information to the local network while DHCP assigns everything except router information. RA can actually also provide prefix information, which makes clients pick a random IPv6. Most small networks will just work fine with RA but DHCPv6 is more powerful in terms of assigning ranges or even do reservations for specific hosts. Therefor i chose to go with RA and DHCPv6 to learn some stuff in the processb.
To configure DHCP for IPv6, enable “Dhcp6s” at the “Setup” -> “IPv6” tab of dd-wrt. Also enable “Dhcp6s custom” and provide configuration like this:
1 | option refreshtime 900; |
The domain-name-servers option is commented out since i chose to distribute DNS resolver information via radvd. Usually that would be a task that gets handled by the DHCP server, but my efforts so far were not working out. For some reason the local address of the router was propagated as DNS server even though i’m not running a DNS cache or forwarder there. This could be some dd-wrt quirk.
I’m distributing search-domain and IPv6 client information via DHCP. As an example i added a specific host that shall get a reserved IPv6. Note that you can assign multiple IPv6 ranges to multiple interfaces if needed. Compared to IPv4 DHCP, hosts are specified via their DUID instead of just their MAC address. The MAC address of the network card is still part of DUID but it gets prefixed by a timestamp that gets generated by software, usually when installing your OS.
Getting your clients DUID is a bit more complicated than just getting a MAC address. Johannes Ullrich posted a nice article about where to find it on various operating systems. Again, wide-dhcp is very picky about syntax, duid 0:1:0:1:1d:9f:e9:8d:20:c9:aa:bb:cc:dd would not work properly while duid 00:01:00:01:1d:9f:e9:8d:20:c9:aa:bb:cc:dd does.
RA is implemented by the radvd service and that gets enabled at the same page. “Radvd config” allows to specify some more details, like this:
1 | interface br0 |
This is a very simple configuration, note that it does not contain any prefix delegation since assigning addresses is done via DHCP. IPv6 DNS resolver configuration is performed via the RDNSS option.
DNS
Next, i headed to my DNS setup. My colleague Bert recently held a great presentation that outlined how important proper DNS is for a good online experience. Virtually any service nowadays depends on DNS and websites use dozens of lookups that suffer from bad DNS performance. Google introduced their Public DNS as a cure-all solution and almost 500M users re-configured their default DNS to point to Google or use it as a default with Android. That service is blazing fast and reliable, no discussion about that. However, Google already knows all your searches - using their DNS also exposes all your other online activity to them, without even using a Google account.
So i gave namebench a spin and tested several DNS servers close to my IPv4 and IPv6 exit points. The results were quite interesting, especially when it comes to speed. The gap between fast and slow services was about 40%. The default IPv4 DNS of my ISP was already good and i kept it as secondary DNS. I added the quickest one as primary and a backup DNS within a different state as tertiary. My local clients get the IPv4/IPv6 of the router as DNS, which acts as a forwarder. I ended with the following servers which were quick, uncensored and reliable:
IPv4
- 193.189.250.100 (Telefonica, Kassel)
- 213.191.74.18 (Hansenet, Hamburg)
- 213.73.91.35 (CCC, Berlin)
IPv6
- 2001:470:20::2 (HE, Fremont)
- 2001:418:3ff::53 (NTT, Denver)